
What Is Cyber Threat Hunting? Definition, Examples and Useful Tools
Cyber attackers succeed because they don’t always set off alarms, and automated systems only catch what they already know to look for. That gap is where cyber threat hunting lives.
A process running two seconds longer than usual or a whisper of traffic sliding through the firewall – those moves hide inside what looks like “normal” activity, and that is what threat hunters go after.
Now, while it all sounds exciting, cyber threat hunting only pays off if you approach it with the right mindset. That is what we are here to build with you. In this guide, we will discuss why threat hunting is important, how it works, the different ways to approach it, and the tools that make it doable.
What Is Cyber Threat Hunting?
Cyber threat hunting is the proactive process of searching through networks, systems, and datasets to detect hidden threats that haven’t triggered any security alerts. Instead of waiting for automated security tools or defences to flag an issue, threat hunters actively investigate suspicious patterns or anomalies that signal an ongoing or potential cyber attack.
It is different from traditional cybersecurity monitoring because it doesn’t rely solely on known indicators of compromise (IOCs). Instead, it focuses on identifying stealthy and sophisticated threats – like zero-day exploits, insider threats, or advanced persistent threats (APTs) – that malicious actors use to evade automated detection systems .
The goal of the cyber threat hunting process is to:
- Reduce the time attackers remain undetected in a system
- Limit potential damage
- Strengthen overall defences by uncovering new tactics and vulnerabilities before they can be exploited.
How Does Cyber Threat Hunting Work: 5 Key Steps
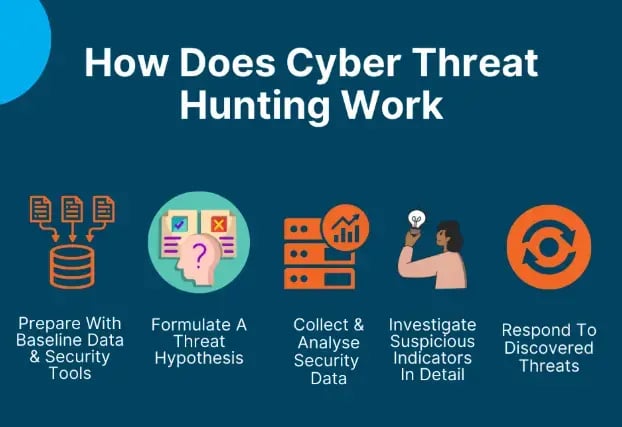
Cyber threat hunting is a structured process where each step builds on the previous one to find threats that traditional tools might miss. Here’s exactly how it works:
1. Prepare With Baseline Data & Security Tools
An effective threat hunting service starts with preparation. Within the Security Operations Center (SOC), security teams first gather baseline data that shows what is “normal” activity in their environment. This baseline can include typical network traffic, user login behaviour, system configurations, and access patterns.
Alongside this, a threat hunter ensures they have the right security tools in place, like:
- SIEM platforms (e.g., Splunk, IBM QRadar) to centralise logs.
- Endpoint Detection and Response (EDR) solutions for detailed visibility into endpoints.
- Threat intelligence feeds to keep up with the latest attack tactics.
This step ensures hunters can differentiate between routine behaviour and potential signs of compromise.
2. Formulate A Threat Hypothesis
Instead of randomly searching for issues, hunters work with a threat hypothesis – a reasoned assumption about how an attacker might target the IT environment.
For example:
- “An insider might be exfiltrating sensitive data during off-hours.”
- “A phishing campaign could have introduced malware that bypassed email filters.”
These hypotheses are based on recent threat intelligence, known vulnerabilities, or observed anomalies. They show where to hunt and how to go about it, so the process works better.
3. Collect & Analyse Security Data
With the hypothesis in place, hunters collect and analyse security data to validate or reject it. Here’s what they do:
- Pull log data from servers, endpoints, firewalls, and cloud services.
- Check for unusual network connections, lateral movement, or privilege escalation attempts.
- Compare current activity against the established baseline.
During data analysis, they may do manual investigation or apply automated correlation rules to spot hidden patterns that attackers use to blend in. Data enrichment services play a critical role here by adding valuable context – like geolocation, device reputation, or threat actor associations – to otherwise raw event data.
4. Investigate Suspicious Indicators In Detail
Once potential red flags surface, hunters move into a deep investigation. They look for IOCs like unusual IP addresses, strange registry changes, or unauthorised privilege escalations.
This phase requires:
- Tracing attacker movement step by step (the “kill chain”).
- Correlating different IOCs to confirm if they point to a coordinated attack.
- Using forensic analysis to reconstruct what happened on compromised endpoints.
The goal is to separate false positives from genuine cyber threats and ensure that time is spent on the right issues.
5. Respond To Discovered Threats
The final step is acting on the findings. If a real threat is found, the response can include:
- Isolating compromised devices from the network.
- Terminating malicious processes or sessions.
- Updating threat detection rules so potential threats are caught automatically in the future.
- Sharing insights with security teams to harden defences and close security gaps.
This step improves the organisation’s overall security posture by turning each hunting exercise into actionable defence improvements.
Pro-Tip: Incident response isn’t only about isolating devices or killing processes. It also comes down to how quickly the right people hear about what is happening. Cyber threat hunting loses its edge if urgent signals don’t reach the right people in time.
One way to close this gap is to set up a dedicated hotline. And to make it more effective, you can also integrate an AI-powered call answering system . That way, if someone notices suspicious behaviour outside office hours, the details still get captured and routed to your security team without delay.
Attackers often time their moves for late nights or weekends, so having an always-on line of communication makes sure the hunt doesn’t stall until morning.
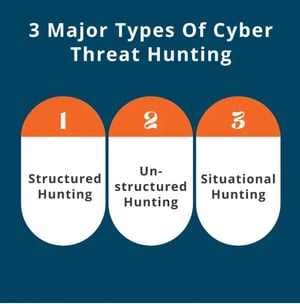
3 Major Types Of Cyber Threat Hunting
Broadly, there are three major types of cyber threat hunting you should know. Beyond protecting organisations, mastering these approaches can also open career opportunities. Skilled hunters are in high demand worldwide, and many professionals use their expertise to make money online through remote security roles, freelance consulting, or specialised training services.
1. Structured Hunting
Structured hunting is a methodical approach where hunters use predefined threat intelligence to look for specific attack patterns or IOCs. The starting point is usually knowledge about attacker tactics, techniques, and procedures (TTPs) gathered from frameworks like MITRE ATT&CK, vendor reports, or past attack cases.
How It Works:
- Cyber threat hunters select a known TTP, such as lateral movement via Remote Desktop Protocol (RDP).
- They analyse logs and endpoint data to identify potential threats matching that pattern.
- If anomalies appear, the hunt continues deeper until the potential threat is confirmed or ruled out.
When To Use It:
- After new vulnerabilities or exploits are disclosed.
- When a certain malware strain or campaign is active globally.
- To proactively check if attackers are using a known method inside your network.
2. Unstructured Hunting
Unstructured hunting is more exploratory and hypothesis-driven. Instead of starting with threat intelligence, hunters begin with an assumption based on their understanding of the environment and possible attack scenarios.
How It Works:
- The hunter forms a hypothesis like: “What if an attacker is using stolen credentials to access admin accounts at unusual hours?”
- Data is gathered from authentication logs, endpoint activity, and cloud services.
- Patterns that deviate from normal behaviour are flagged for investigation.
When To Use It:
- When no specific threat intelligence is available.
- To test the resilience of systems against possible attack paths.
- To identify unknown or novel threats that traditional tools may not catch.
3. Situational Hunting
Situational hunting is event-driven and happens in response to a particular trigger or incident. Instead of being routine, it is launched when a new situation arises that could indicate risk.
How It Works:
- A trigger occurs, like a phishing campaign targeting employees or a sudden spike in failed login attempts.
- Threat hunters pivot to investigate the specific event by looking at network traffic, endpoint alerts, and email gateways.
- The hunt continues until the scope of the incident and potential impact is fully understood.
When To Use It:
- After suspicious activity is reported by employees or flagged by monitoring tools.
- During ongoing campaigns targeting similar organisations.
- When responding to industry-wide alerts about fresh attack strategies.
6 Practical Examples Of Cyber Threat Hunting
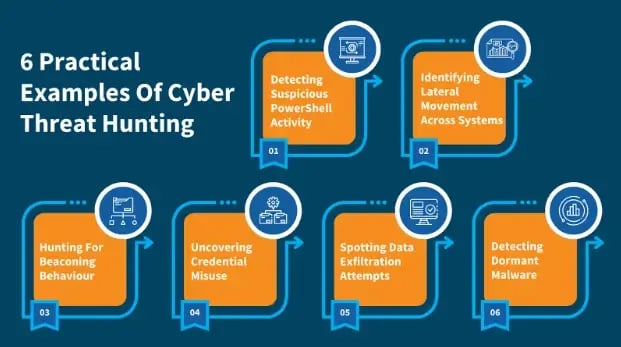
Here are 6 practical examples that show how security teams apply hunting techniques in real-world scenarios.
1. Detecting Suspicious PowerShell Activity
Attackers often abuse PowerShell because it is built into Windows. This makes it a powerful threat hunting solution for executing malicious scripts without triggering antivirus alerts. Detecting it early can stop ransomware deployment, privilege escalation, or backdoor installation before attackers gain full control of systems.
How Threat Hunters Do It:
- Collect command-line logs from endpoints.
- Search for unusual PowerShell commands like encoded scripts, obfuscated strings, or commands that launch from unexpected directories.
- Compare activity to normal administrative usage to spot anomalies.
Example Tool Use: EDR solutions like CrowdStrike or Microsoft Defender can monitor command-line activity and flag unusual PowerShell behaviour.
2. Identifying Lateral Movement Across Systems
Once attackers compromise one machine, they jump from system to system to expand their access and reach critical assets. Catching lateral movement quickly prevents threat actors from moving deeper into sensitive areas, like domain controllers or financial databases.
How Threat Hunters Do It:
- Monitor authentication logs for abnormal patterns (e.g., a standard user account logging into multiple servers).
- Look for excessive use of remote administration tools (e.g., PsExec, RDP).
- Correlate login times, locations, and methods to detect credential misuse.
Example Tool Use: SIEM platforms like Splunk or QRadar help correlate authentication events across multiple systems.
3. Hunting For Beaconing Behaviour
Malware often “beacons” – sending regular outbound traffic to a command-and-control (C2) server to receive instructions. This communication is usually subtle and disguised as normal web traffic.
Finding beaconing early can reveal hidden malware infections that might otherwise stay dormant until activated.
How Threat Hunters Do It:
- Analyse network logs for recurring traffic patterns (e.g., pings every 30 seconds to the same external IP).
- Use frequency analysis to identify traffic that looks too regular compared to human-driven activity.
- Cross-reference with known malicious IP addresses from threat intelligence feeds.
Example Tool Use: Network monitoring tools like Zeek or Suricata can detect abnormal outbound traffic patterns.
4. Uncovering Credential Misuse
Stolen or misused credentials are a top attack vector as they lead to privilege escalation and unauthorised access. Threat hunting teams look for unusual patterns that indicate misuse.
How Threat Hunters Do It:
- Track failed and successful login attempts across accounts.
- Flag logins from unusual geolocations or at odd hours.
- Look for privilege escalation where a normal account suddenly gains admin rights.
Example Tool Use: Identity security tools like Okta or Microsoft Azure AD logs can highlight irregular account usage.
5. Spotting Data Exfiltration Attempts
Attackers don’t just infiltrate systems – they try to extract sensitive data (customer records, intellectual property, financial details). Exfiltration is usually disguised as normal traffic.
Even if attackers bypass defences, stopping them before data leaves the network protects against a full-blown data breach. That not only protects against reputational damage but also will help you retain customers who value security and reliability above all else.
This risk is amplified in industries like healthcare support, where personal and medical details are processed daily. A good example is the MedicalAlertBuyersGuide , which connects seniors and caregivers with emergency alert solutions. At first glance, it is simply a consumer resource. But from an attacker’s perspective, it is more attractive than many high-profile targets.
The reason is simple: the combination of sensitive personal data, recurring financial transactions, and indirect links to hospitals and insurers. Unlike a bank, which expects constant attacks and invests heavily in defences, consumer-facing healthcare platforms are under-protected. That makes them a softer entry point into the broader healthcare ecosystem.
For threat hunters, this niche demands sharper focus. Exfiltration attempts involving seniors’ addresses, health-related preferences, or billing records can slip past standard alerts because the data doesn’t always trigger high-priority alarms.
What makes it more critical here than in other industries is the dual consequence: a single unnoticed breach doesn’t just result in financial theft, it also erodes trust in services that vulnerable populations rely on for safety.
How Threat Hunters Do It:
- Monitor large or unusual outbound file transfers.
- Inspect for encryption or compression methods used to package stolen data.
- Compare traffic volume to baseline activity – sudden spikes can mean exfiltration.
Example Tool Use: Data Loss Prevention (DLP) systems can alert on suspicious data movement.
6. Detecting Dormant Malware Or Persistence Mechanisms
Attackers often install malware that stays hidden (dormant) until triggered, or they use persistence mechanisms (e.g., registry modifications, scheduled tasks) to maintain long-term access. By removing dormant malware and persistence mechanisms, hunters prevent attackers from regaining access even after an initial compromise is cleaned up.
How Threat Hunters Do It:
- Scan endpoints for unusual autorun entries, registry keys, or scheduled tasks.
- Hunt for unsigned or rarely used binaries sitting idle on systems.
- Compare system state against a known clean baseline to detect hidden implants.
Mrityunjay Singh
Leave a comment
Your email address will not be published. Required fields are marked *

